
What is OAuth 2.0
OAuth (Open Authorization) is an open standard that allows users to authorize third-party websites to access the information they store on another service provider without providing usernames and passwords to third-party websites or sharing their data with all content.
Example: For example, we often see "Google Login, Facebook(META) Login, Twitter login, GitHub login" on major websites. Using these platforms, we can use these platforms to log in without registering a new account on a third-party website. method.
OAuth2.0 Login Process
For the authorization process of the OAuth2.0 protocol, please refer to the following flowchart The client refers to third-party applications Resource Owner refers to the user Authorization Server is our authorization server Resource Server is an API server
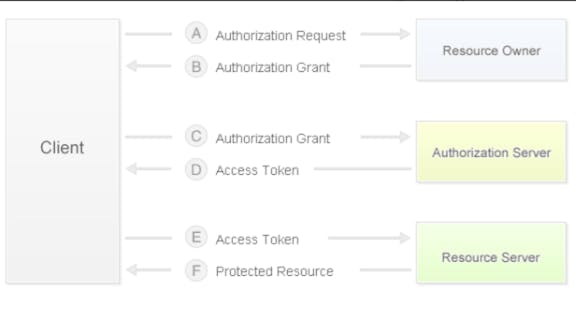
The whole process is divided into six steps A~F:
A: The Client sends an authentication request to the Resource Owner. B: The Resource Owner authorizes the Client's request and issues an authorization token, Authorization Code, to the Client. C: The Client carries the Authorization Code to initiate an authorization request to the Authorization Server. D: The Authorization Server authorizes the Client's request and issues an Access Token to the Client. E: The Client carries the Access Token to request user information resources from the Resource Server. F: After the Resource Server verifies that the Access Token is legal, it sends the user information resource back to the Client.
Attack Method
CSRF binding hijacking
redirect_uri bypass authorization hijacking
CSRF Binding Hijacking
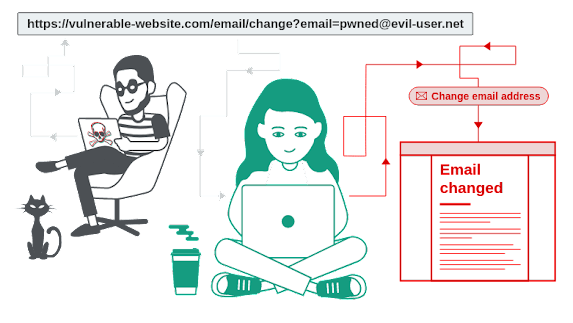
The attacker grabs the authentication request to construct a malicious URL and deceives the logged-in user of the server to click (for example, through QQ message/WeChat message/website internal letter/mail, etc.)
At this time, as long as the user clicks on the malicious URL, the authentication will be triggered. After the authentication is successful, the user's account will be bound to the attacker's account, and the attacker can log in to the bound account through OAuth.
- Defense method:
- This is the client's problem.
- OAuth 2.0 provides the state parameter for CSRF defense.
- When the authentication server receives the state parameter, it will return it to redirect_uri as is.
- The client receives this parameter and verifies whether it is consistent with the previously generated value.
redirect_uri bypass Authorization Hijacking
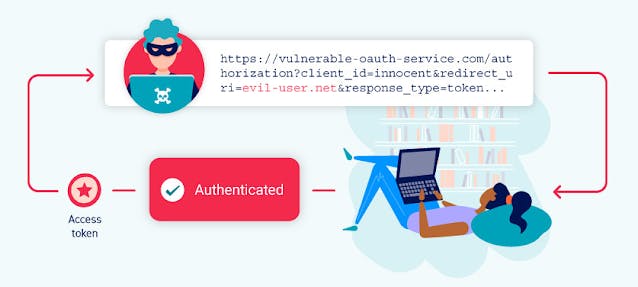
According to the OAuth authentication process, the authentication server will obtain the application data according to the client_id and judge whether the redirect_uri is legal.
If passed, the user authorization credentials will be forwarded by the server to the address corresponding to redirect_uri.
If this address can be controlled by the attacker and forged as his own redirect_uri address, and then induce the user to send the request, the obtained credentials will be sent to the attacker's forged callback address.
An attacker can use this credential to log in to the user account, resulting in authorization hijacking. Malformed URL Bypass Method important point: auth.app.com = The callback address saved by the authentication server evil.com = malicious domain auth.app.com.evil.com evil.com?http://auth.app.com auth.app.com@evil.com evil.com?@http://auth.app.com auth.app.com@evil.com evil.com\auth.app.com evil.com:\auth.app.com evil.com.auth.app.com evil.com:@http://auth.app.com evil.com#http://auth.app.com evil.com\auth.app.com /evil.com?http://auth.app.com http//evil.com?http://auth.app.com
The core of the bypass method using malformed URLs is to make the callback address of the authentication server feel like a normal request Cross-Domain Bypass Steal the token from the referer by using the URL jump of the trusted domain
Example 1: The website has an arbitrary URL jump vulnerability, which can be exploited to construct the following vector
The authentication server sends the credentials to redirect.php through the GET method. At this time, redirect.php executes a URL jump and accesses evil.com. The attacker records logs in evil.com and extracts them from the referrer field in the request header. This certificate can be used to authorize the login.
Example 2: Stealing token from referer using cross-domain request
When we cannot bypass the judgment rule of redirect_uri, we can use a cross-domain request to steal the token from the referer.
The redirect_uri is limited to only app.com, but there are places where we can operate the website, such as:app.com/article/1.htmlAllows users to post articles and insert pictures and the like.
Then I can embed external images from evil.com in the article.
For example this: 
After the user is authorized, the request may be:app.com/article/1.html?code=xxxxxxxxThen jump to this article address, then load the external image, then evil.com records the log, and extracts the credential from the referrer field in the request header, and you can log in through the credential.
